1. The Problem: When Fast Work Creates Risk Gaps
Bon, a small but fast-moving growth team, partners with ambitious clients to scale marketing, design, sales and growth strategies. With their high client volume and many projects, Bon constantly handles sensitive files between different shared access points.
But like many lean teams, Bon faced a familiar problem: Cybersecurity risks were slipping through. For example:
- One team member clicked a suspicious link without confirming with stakeholders
- Files were shared over unsecured channels for convenience
And it wasn’t because people ignored the risks. It was because cybersecurity kept getting framed as “IT’s job”, and cybersecurity knowledge is often seen as dry, lengthy, and hard to understand, so even when company sent them the basic courses for reference, people are hesitant to engage with them.
So, F.Learning Studio designed a course for Bon to move cybersecurity beyond compliance, a course that is built to tackle common blockers!
2. Our Approach: Turning Cybersecurity from a Dry Document into a Daily Mindset
We designed this course to shift the narrative, from long, forgettable content to real-world awareness that fits Bon’s pace and reality.
With multiple tools, shared access, and fast project turnover, Bon’s team faces more entry points than ever — and fewer chances to stop and think. At that point, awareness is no longer optional; it is their first line of defense.
The Cybersecurity Course will help Bon’s members reflect and self-wonder:
- Spot realistic threats — the kind that show up in Lark, Google drives, Figma or a casual email
→ “That link your coworker sent? It could be a phishing attempt. - Think in terms of business risk, not vague fear
→ “What’s the real cost if this system goes down — and how do we prevent that?” - Know what to do when something goes wrong — and who owns what
→ “If something goes wrong, who leads? Who communicates? Who coordinates?” - See themselves as part of the defense system instead of memorizing policies
3. Designing for Impact, Not Just Information
How we turned frameworks into visuals, threats into stories, and learning into habits.
Bon’s challenges aren’t unique — many teams struggle with unclear roles, dry content, and hidden risks in daily habits. That’s why this approach works across companies.
To make it stick, F.Learning customizes scenarios and prompts to match each team’s reality, so that every team sees themselves, with their own characteristics in the learning.
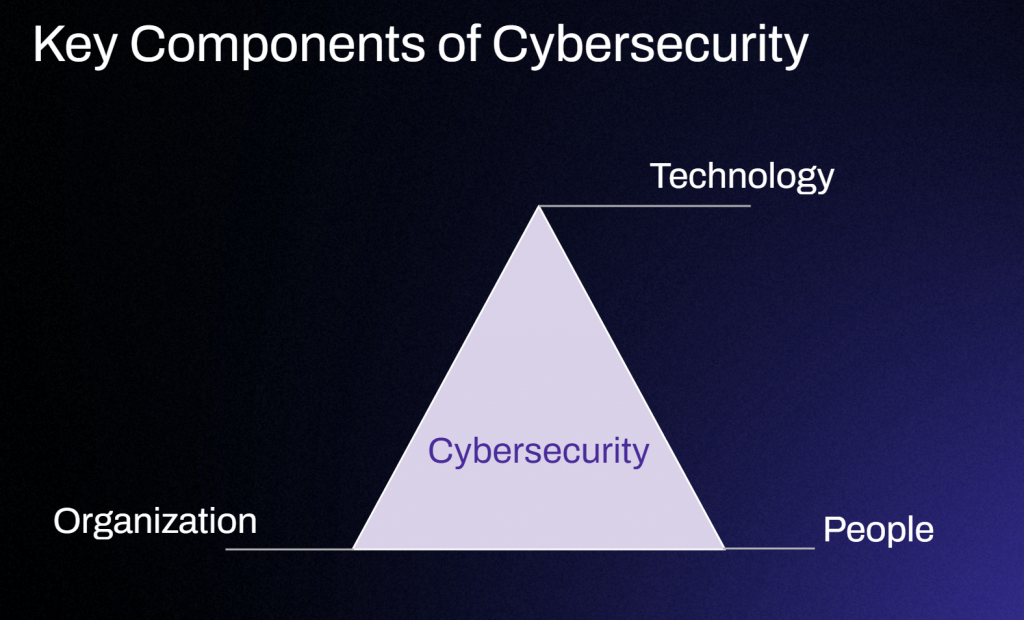
3.1. Turn Frameworks into Visuals
We brought key concepts to life through easy-looking models and realistic stories (E.g., financial system leaks, fake emails,…). By that, Bon’s learners can find it easier to build mental models — tapping into the fact that humans are naturally visual learners.
3.2. Make Risks and Costs Feel Real: Rooted from Everyday Examples
We opened up with real scenarios that are relatable to everyone in the company:
- The company skipped a system update — and hackers found the weak spot.
- An employee clicked a fraud email and leaked customer data.
- A former staff member downloaded sensitive files.
3.3. Use Stories to Trigger Self-Reflection
We built the course around bite-sized, relatable scenarios that reflect how cybersecurity risks actually show up in teams like Bon — not in theory, but in the flow of real work.
Each scenario is paired with a simple question that gets the team thinking, like:
- “If someone clicks a suspicious link again, who handles it, and how fast do we respond?”
- “What happens if a shared Figma or Google Drive folder is accidentally exposed?”
- “Do we know which laws apply when we work with international brands?”
And suddenly, the content wasn’t theory — it became a wake-up call.
3.4. Build Habits, Not Just Awareness
F.Learning Studio focused on helping Bon build small, repeatable actions through awareness of scenarios and reflection questions:
- Double-checking links before clicking
- Questioning how files are shared
- Verifying vendor security policies
These “tiny defaults” became daily defense behaviors, because knowledge fades, habits stick.
4. What Shifted Inside Bon?
How small mindset shifts at Bon led to smarter habits, faster responses, and shared ownership.
This wasn’t just another training — it was a reset. Here’s what changed inside Bon’s team:
- All members stopped assuming “someone else will fix it”. Even non-technical team members started spotting risks early
- Teams created simple guidelines for what to do if something goes wrong, including who updates clients or locks down shared links
- Leaders began budgeting for security as part of growth — not just for tools, but for team habits and readiness
- And new prompts appeared in team chat: → “Did we clear access for that freelancer?” → “Can we double-check the link before sharing?”

Ready to Train Your Team Differently?
If you want your people to be your first line of defense — not your biggest vulnerability — this is where to start.
If you’re in HR, IT, compliance, or a leader — and want your team to stop being the weakest link — this is the kind of course that drives change.
We’d love to tailor it to your context. Let’s build a culture where cybersecurity is everyone’s job — and everyone feels confident doing it.








![5 Best Animated Video Production Companies [Update 2023] 10 review 5 animated video production house](https://flearningstudio.com/wp-content/uploads/2021/06/312x200-5-420x500.jpg)





