As hackers become smarter every day, staying a step ahead of cyber threats is essential, and cybersecurity simulation training provides the perfect practice ground. This type of training offers hands-on experience, helping employees recognize threats and respond quickly. In this article, we’ll explore the importance of cybersecurity simulation training and a step-by-step guide to creating a comprehensive training program.
- What is Cybersecurity Simulation Training?
- Benefits of Cybersecurity Simulation Training
- Types of Cybersecurity Simulation Training
- How does Cybersecurity Simulation Training Work?
- 10 Steps to Set up a Cybersecurity Simulation Training Program
- Partner with F. Learning Studio to Elevate Cybersecurity Simulation Training
- Conclusion
What is Cybersecurity Simulation Training?
Cybersecurity simulation training is a type of training involving realistic scenarios that simulate cyber attacks. This allows participants to practice identifying, responding to, and mitigating these threats without the risks associated with real attacks.
Key components of cybersecurity simulation training:
- Realistic scenarios: Participants engage in exercises that replicate common cyber threats, such as phishing attacks, ransomware incidents, or data breaches.
- Hands-on practice: Training often includes role-playing exercises or virtual labs. These activities allow individuals to interact with simulated environments that replicate their actual systems and networks.
- Feedback and improvement: After simulations, participants receive feedback on their performance, so they can learn from mistakes and improve their skills.
Benefits of Cybersecurity Simulation Training
Realistic training experience
The best part about cybersecurity training is that it takes employees right into action, throwing them into scenarios that feel just like real cyber-attacks. This hands-on and immersive practice helps them spot vulnerabilities, learn the tricks cybercriminals use, and master their response strategies.
So, when a genuine cyber event happens, they’re not just ready—they’re prepared to outsmart the attack.
Proactive defense strategy
Simulated attacks give organizations a way to stay ahead of cyber threats. Instead of waiting for a real breach to reveal weaknesses, regular cybersecurity simulation training helps to catch vulnerabilities early. This lets businesses tighten up defenses before attackers even get close. With a proactive strategy like this, companies can reduce the risk of a successful attack.
Enhance employee awareness
Human error is a leading cause of data breaches, but with the right training, employees can become your strongest defense. By being exposed to realistic simulated attacks, your employees can spot and respond to attacks effectively. These simulations sharpen their instincts, teaching them to recognize suspicious activity, avoid phishing traps, and react under pressure.
Improve compliance and regulation
Many industries have strict cybersecurity standards to meet, and compliance isn’t optional. By running regular simulations, companies can show they have strong security measures in place. Plus, these simulations make audits smoother, showing regulators that the organization is serious about security and well-equipped to meet compliance requirements.
Types of Cybersecurity Simulation Training
Cybersecurity simulation training comes in various forms, so you may find it hard to make the decision. Below we collected the most popular ones to help you choose the right approach
| Training | Description | Focus | Example |
| Tabletop Exercises | Discussion-based sessions analyzing potential cyber-attack scenarios and response actions | Testing incident response and decision-making processes | Simulating a data breach to discuss containment steps and notifications |
| Blue & Red Team Exercises | Defensive training where the “Blue Team” (defenders) identify and respond to simulated attacks, defensive exercises with a “Red Team” (attackers) simulating attacks to expose security weaknesses | Strengthening detection and response capabilities & Identifying security weaknesses through testing | Blue team exercise: A simulated network attack requiring the team to identify, analyze, and respond.Red team exercise: Ethical hackers attempt to breach the firewall or access sensitive data |
| Red Team Exercises | Offensive exercises with a “Red Team” (attackers) simulating attacks to expose security weaknesses | Identifying security weaknesses through testing | Ethical hackers attempt to breach the firewall or access sensitive data |
| Phishing Simulations | Controlled phishing emails sent to test employees’ ability to recognize and report them | Increasing awareness of phishing tactics | Sending a fake email that mimics a phishing attempt to assess response |
| Social Engineering Awareness Training | Training focused on tactics used in social engineering to manipulate or deceive employees | Building awareness of social engineering methods | A simulated call from “IT support” asking for login credentials |
| Incident Response Training | Hands-on exercises guiding teams through the steps of responding to an incident | Improving speed and effectiveness of incident responses | A ransomware scenario where the team isolates systems, communicates, and initiates recovery efforts |
| Technical Cyber Exercises | In-depth technical simulations requiring skills in threat analysis and mitigation | Developing technical expertise in cybersecurity tools | A malware outbreak simulation requiring identification, quarantine, and eradication |
| Cyber Threat Hunting | Proactive exercises where teams search for hidden threats within the network | Enhancing threat detection skills for advanced threats | Searching for Indicators of Compromise (IoCs) in logs to identify signs of unauthorized activity |
How does Cybersecurity Simulation Training Work?
To help you better implement cybersecurity simulation training into practice, below is an overview of how it works:
- Planning and scenario design: Cybersecurity experts design realistic attack scenarios that reflect the types of threats most likely to impact your organization, such as phishing attempts, ransomware attacks, or insider threats.
- Training environment setup: A safe, isolated training environment is created to simulate the cyber-attack without risking the organization’s actual systems. This virtual space allows employees to respond to threats without any real danger.
- Interactive simulation: Employees participate in the simulation, where they encounter various stages of a cyber-attack, like a suspicious email or system breach. They practice identifying signs of an attack, understanding the scope, and taking immediate action.
- Real-time feedback and coaching: Throughout the simulation, employees receive real-time feedback. This guides them on proper response actions and helps them understand what they did well or could improve.
- Debrief and analysis: After the simulation, teams review their actions with cybersecurity trainers, analyzing what went right, where they hesitated, and how their responses could be faster or more effective.
- Reporting and compliance documentation: Post-training requires reports showing that employees have been trained on specific scenarios. This documentation is useful for compliance audits and shows a proactive approach to security.

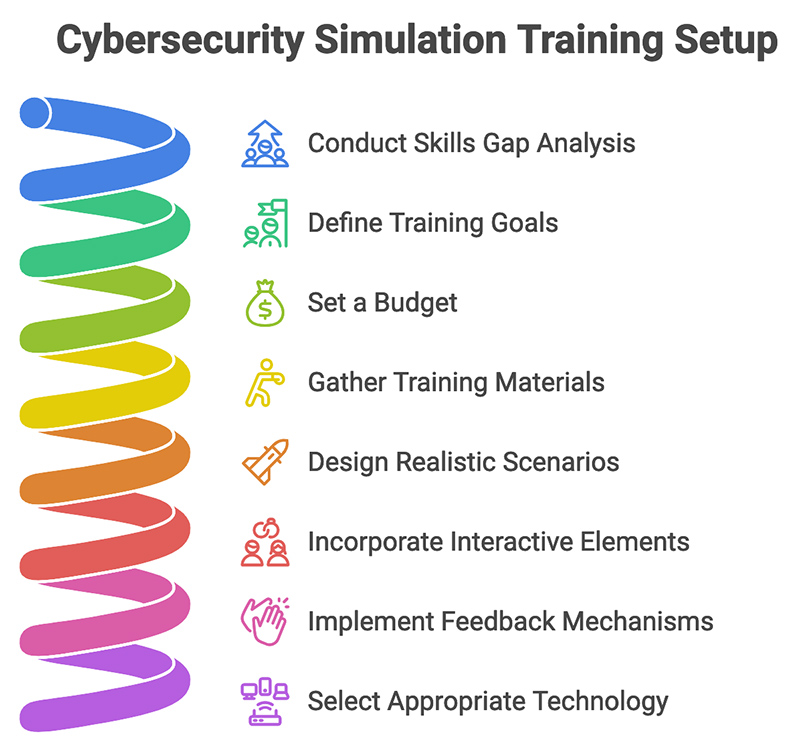
10 Steps to Set up a Cybersecurity Simulation Training Program
If you’re unsure how to get started, that’s totally fine. To give you a roadmap for building a comprehensive training program, here are the 10 steps that guide you through the process:
- Conduct a skills gap analysis: Assess the current cybersecurity knowledge and skills of your employees to identify areas that need improvement. This helps tailor the training to address specific weaknesses.
- Define training goals: Establish clear objectives for the training program, such as improving threat detection, enhancing incident response, or increasing overall cybersecurity awareness among employees.
- Set a budget: Determine the financial resources available for the training program, including costs for materials, technology, and any external trainers or consultants.
- Gather training materials: Collect relevant resources, such as manuals, online courses, and simulation tools that will be used during the training sessions.
- Design realistic scenarios: Create engaging and relevant scenarios that reflect potential cyber threats your organization may face. These should be challenging yet achievable to keep participants engaged.
- Incorporate interactive elements: Use interactive methods like role-playing, gamification, or hands-on labs to make the training more engaging and effective in retaining participants’ attention.
- Implement feedback mechanisms: Establish ways to gather feedback from participants during and after the training sessions. This can include surveys or debrief discussions to assess their understanding and experience.
- Select appropriate technology: Choose suitable tools and platforms for delivering the training, such as simulation software or virtual labs that can replicate real-world cyber environments.
- Pilot test the program: Run a pilot session with a small group of employees to evaluate the effectiveness of the training materials and methods. Use this opportunity to make adjustments based on participant feedback.
- Evaluate and adjust: After full implementation, regularly assess the program’s effectiveness by measuring outcomes against the defined goals. Make necessary adjustments based on feedback and evolving cybersecurity threats.
Partner with F. Learning Studio to Elevate Cybersecurity Simulation Training
Offer customized videos for cybersecurity simulation training
We, F. Learning Studio, believe that the training program should resonate with learners, so we tailor our solutions to fit your unique training needs, audience, and budget. Forget generic content—we work with you to build videos that speak directly to your team, covering real-world cybersecurity challenges in a way they’ll remember.
By focusing on what matters most to your organization, we help you deliver training that’s effective, targeted, and impactful.
Expert in animation and interactive design for training
Our team at F. Learning Studio knows that cybersecurity can seem dry and technical, so we bring it to life with top-notch animation and interactive design. We make complex topics easy to grasp, using engaging visuals and hands-on elements to keep learners tuned in.
It’s all about creating experiences that go beyond basic learning, ensuring employees walk away with a clear understanding of how to handle real cybersecurity threats.
Supportive and streamlined work process
Our flexible, structured process ensures your cybersecurity training solution is delivered efficiently, saving you time and resources. We keep you informed every step of the way, creating a smooth and effective journey to launch training that prepares your team to tackle cyber threats head-on.
interested to know more?
Glad you like us! Book a consultation call with us to explore how to kick start your animation project.
Conclusion
Investing in cybersecurity simulation training is necessary to equip your team with knowledge and skills that help them recognize and respond to real threats. This hands-on approach not only enhances their ability to handle potential attacks but also builds a proactive culture of security across your organization.
Whether you’re just starting to build a plan or looking to elevate your current training program, let’s make it effective, engaging, and impactful. F. Learning is here to help you achieve this. Partner with us to create tailored, engaging visuals that bring cybersecurity concepts to life, making training memorable and results-driven.
- WhatsApp: (+84) 378 713 132
- Email: [email protected]
- Fanpage: https://www.facebook.com/f.learningstudio
- LinkedIn: https://www.linkedin.com/company/f-learning-studio/

Sean Bui, the founder and creative director of F.Learning Studio, is a respected leader in the e-learning and multimedia production industry. With over 10 years of experience, he has dedicated his career to helping organizations create engaging and impactful learning experiences.
Under his leadership, F.Learning Studio has grown into a trusted partner for organizations in the education, healthcare, and corporate training sectors, producing over 2,000 minutes of educational animation.